Security is becoming an extremely critical phenomenon of modern business operations, with organizations operating under increasing threats and vulnerabilities in the digital realm. Given the growing importance of security, it will not be incorrect to state that DevSecOps is making noise amongst most businesses. Given its popularity and potential, most businesses, right from start-ups to multinationals are banking on its advantages. It is an approach that works on the missing link called security to ensure the product development process is carried out with utmost safety. Additionally, an intriguing aspect of DevSecOps is its symbiotic relationship with cybersecurity.
Today, modern approaches are redefining conventional development procedures in the rapidly evolving field of technology, where innovation is a constant.
DevOps has embraced software development with best practices and techniques, enabling the development and operations teams to realize faster, more reliable, and good-quality software development processes. The most significant evolution in software development is the integration of security into DevOps, building a culture where security becomes a vital part of the development process. Integrating development, security, and operations into a combined security approach is known as Development Security Operations (DevSecOps). DevSecOps takes the lead and transforms the way we think about security in product development. DevSecOps effectively integrates security practices throughout the entire development process. It is above and beyond the conventional model by making security considerations a top priority from the early stages of the project, encouraging a proactive approach to mitigate potential risks. It encourages cooperation between the operations, security, and development teams, setting up a common front against security risks.
Technology is a fast-paced field, and DevSecOps revolutionizes security and development tactics by fostering a proactive and cooperative environment. DevSecOps radically changes the game by putting security first from the beginning and making sure that products are designed to withstand new threats. Read the blog to explore on the significance of DevSecOps in realizing product security.
Implementing DevSecOps Best Practices in Software Development Lifecycle (SDLC)
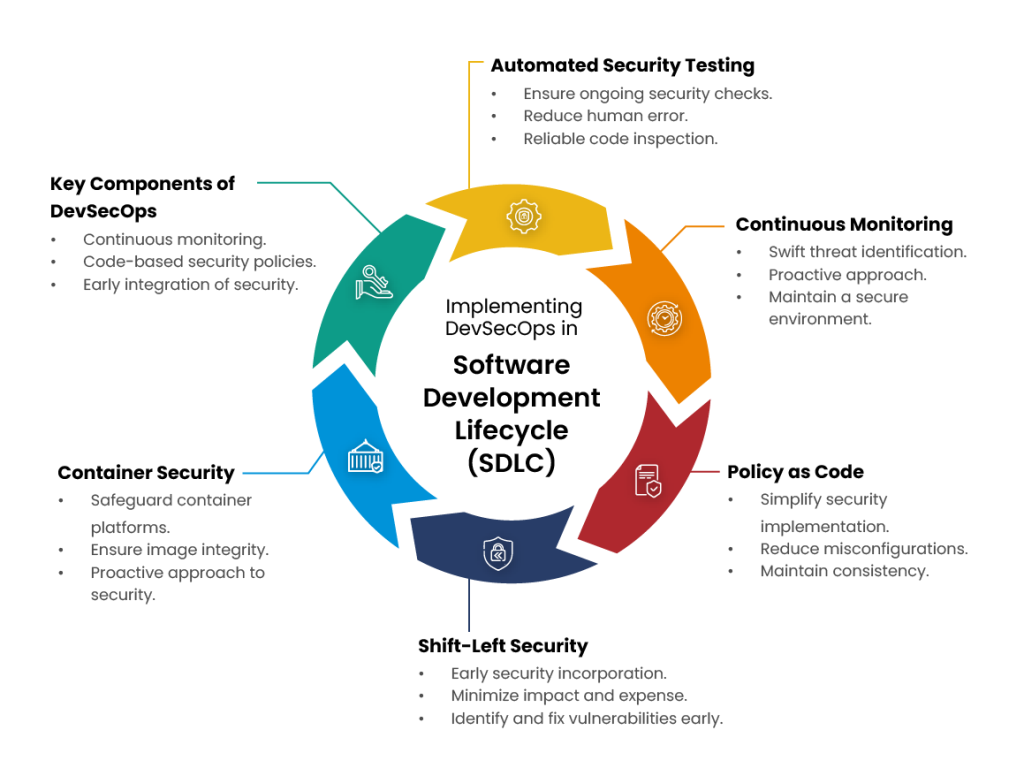
To build a robust development process, DevSecOps prioritizes early security measures, policy integration, automated testing, container security, and continuous monitoring with a focus on product security. By strengthening resistance to changing threats, these procedures protect products and data integrity.
Automated Security Testing: An essential component of DevSecOps deployment is automated security testing. Enterprises may guarantee ongoing security checks throughout the software development process by including automated technologies in the development pipeline. It reduces the possibility of human mistakes and offers reliable code inspection.
Continuous Monitoring: To identify and address security threats quickly, DevSecOps places a strong emphasis on the ongoing observation of infrastructure and applications. This proactive approach ensures that any questionable activity or possible security breaches are quickly discovered. By addressing security concerns as they emerge rather than waiting for sporadic evaluations, continuous monitoring enhances the organization’s ability to maintain a secure environment.
Policy as Code: This technique simplifies the administration and implementation of security measures by exposing security policies as code. Enterprises may reduce the risk of misconfigurations and maintain consistency across several settings by converting security policies to code. It improves overall system security and is in line with the DevSecOps idea of seamlessly integrating security into the development process.
Shift-Left Security: The idea of “shift-left” security is supported by DevSecOps, which encourages the early incorporation of security procedures into the development process. This includes handling security issues early on in the project rather than as a stand-alone stage. Enterprises may minimize the possible effect and expense of security issues later in the development lifecycle by identifying and fixing vulnerabilities early on.
Container Security: Ensuring container security is a critical component of DevSecOps, as containerization becomes more common in software development. To address issues such as safeguarding container orchestration platforms and guaranteeing the integrity of container images, organizations employ security measures that are tailored to containerized applications. By taking a proactive approach, companies may be able to utilize containerization’s advantages without sacrificing security, as technology advances.
Continuous monitoring, code-based security policies, early integration of security measures, and specific security considerations for containerized systems are the main components of DevSecOps practices. These procedures make the software development process more secure and effective.
The Roles of DevSecOps Teams in Supporting Product Security
Collaboration between security teams, operations, and developers is critical when it comes to product security. The integration of security from coding to deployment is emphasized by DevSecOps, which strengthens products against new threats.
Developers: The DevSecOps ecosystem relies heavily on developers since they create secure code and include security procedures in the development process. Beyond functionality, they are also accountable for considering potential vulnerabilities and fixing them at the code level.
Security Teams: Within the DevSecOps architecture, security policies are defined and implemented by specialized security teams, to set compliance guidelines, conduct risk assessments, and mentor developers in secure coding techniques. Security experts assist in building a strong defense against any claims by working closely with the development and operations teams.
Operations Teams: It plays a key role in incorporating security measures into the deployment process and concentrate on keeping the entire system infrastructure secure and keeping an eye on things to quickly identify and address any security incidents. The smooth integration of security issues into the operational facets of product development is ensured by this cooperative effort.
Collaboration Specialist: DevSecOps is one of the most important aspects of DevSecOps, ensuring that various teams are effectively communicating and working together. Collaboration experts serve as intermediaries, creating a collaborative atmosphere that enables development, security, and operations teams to collaborate effectively.
Automation Specialists: Since automation is the foundation of DevSecOps, they focus on setting up and executing automated security testing procedures, to incorporate security technologies into the development process so that the codebase is continuously inspected and evaluated. The chance of security breaches by automating regular security checks, helps with vulnerability early identification and mitigation.
DevSecOps team advocates for the entire security posture. The integration of security into all aspects of the product development process, from coding to deployment, is achieved through the collaboration of developers, security teams, operations teams, collaboration specialists, and automation experts. By working together, we can ensure that security is regarded throughout the entire development process, rather than just as an initial thought.
Challenges and Considerations of DevSecOps Implementation:
Addressing, encouraging shared accountability, and showcasing success stories are all important components of overcoming cultural resistance. Compliant automation technologies and gradual deployment are necessary to manage integration complexity. Cross-functional training and certifications can help close skill gaps. This is why it is essential to have a fair understanding of the challenges.
Resistance to a Cultural Shift:
One of the major obstacles to implementing DevSecOps in organizations is resistance to cultural alteration. Enterprises can address this by providing extensive training programs that inform teams of the advantages of DevSecOps. Cultural obstacles can be overcome by highlighting the shared accountability for security and establishing a collaborative environment through cross-functional teams. A more seamless cultural shift can be achieved by promoting success stories of DevSecOps implementations within the company and maintaining constant contact.
Complexity of Integration:
It is challenging to integrate security into the development process, particularly in settings where workflows already exist. Enterprises should take an incremental approach to integration to solve this, beginning with pilot projects and gradually extending DevSecOps techniques throughout the entire development pipeline. Automated automation technologies that are compatible with current development tools can also reduce the complexity of the integration process.
Skillset Gaps:
It can be utilized by providing tools for obtaining relevant certifications and encouraging a culture of lifelong learning. Developing a comprehensive understanding of security measures is facilitated by cross-functional training that fosters collaboration between security specialists and other teams.
A planned and incremental strategy is necessary to tackle the problems of competence shortages, integration difficulty, and opposition to cultural shifts. Enterprises may effectively manage these hurdles and enjoy the advantages of a secure and efficient DevSecOps implementation by making investments in education, communication, and cooperation.
Future Trends and Opportunities in DevSecOps
DevSecOps is promising and is rapidly becoming crucial for businesses to operate safely and securely. Since this technology is growing at rocket speed, it is vital to stay updated with what’s trending to use it for its best advantage.
Artificial Intelligence (AI) and Machine Learning (ML) Integration: The predictive analytics capabilities of DevSecOps will be improved by AI and ML algorithms, allowing for automated threat identification and response. By observing trends and abnormalities in real-time, this integration will enhance the security posture and provide a more proactive response to altering cybersecurity threats.
DevSecOps as a Service (DaaS): The development of DevSecOps as a Service is an emerging trend. Small businesses will be able to execute this approach because it allows them to contract with specialized service providers to handle their DevSecOps operations. DevSecOps as a Service makes it possible for enterprises with little internal experience to deploy strong security procedures with ease by providing access to professional resources and technologies.
Advances in Container Security: DevSecOps methods will prioritize container security more heavily due to the increasing popularity of containerization. To meet the special difficulties in securing containerized applications, advanced container security solutions will be created. This includes safeguarding container orchestration systems, enhancing the integrity of container images, and safeguarding the containerized development and deployment process.
Evolution of cloud-native security: DevSecOps will adjust to meet the unique security issues encountered by cloud environments as cloud-native technologies continue to evolve. Secure cloud-native development will be the main emphasis of future DevSecOps techniques, guaranteeing that cloud platform apps are resistant to new threats. As enterprises depend more and more on cloud services to provide their IT infrastructure flexibility and scalability.
Conclusion
In the current era of constantly changing cyber threats, DevSecOps has become an indispensable ally in bolstering product security. This strategy’s ongoing, cooperative, and proactive characteristics are changing our understanding of and attitude toward security in the digital sphere. As we move forward, companies looking to stay ahead of any risks will find that adopting DevSecOps is not only an option but a requirement.
Calsoft integrates security principles effortlessly early in the application development cycle, enabling enterprises to strengthen their DevOps pipeline. Our knowledge guarantees the smooth fusion of industry standards with top security offerings. This strategy protects enterprises from any dangers by ensuring performance optimization without sacrificing critical security and compliance requirements.