SSDs and Application Performance: What’s the connect?
Before I even start getting into the details of SSD and application performance, a foreword about what is the intent behind writing this post. This post will…
SDN Controller Performance Challenges – 1
In our earlier blog, you learned about the basics of SDN as well as its growing market opportunities.But one factor that can falter the SDN promise is…
Security Holes – Part 2
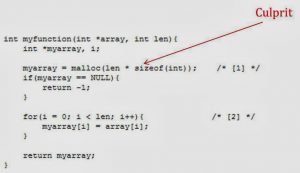
In Part-1 of this post we spoke about security holes and 2 sources of vulnerabilities: Buffer Overflow and SQL Injection. We will cover next 3 sources in…
Getting along with Software-Defined Networks
The latest topic in enterprise networking is software-defined networks (SDNs), which increase the intelligence of the core network making it more receptive to overall IT and business…
VHDX: The New Wave in Virtual Hard Disk Formats
A bit about VHDs Virtual hard disk or VHD is a way to provide storage medium for virtual machines, which is represented as a disk image…
