Do you feel flooded with security alerts daily? Do you need help keeping up with the data overload? One critical alert might be overlooked in such instances, leading to a severe security breach.
Why is this happening? Well, the fact is that the digital world is expanding—there are more devices and data. The threats are getting more sophisticated. The old ways of dealing with security just don’t suffice anymore. This is the role of security automation.
Automation in security refers to using technology to perform repetitive security tasks. It is also known as automated security, which refers to the immediate detection and resolution of security alerts without constant manual intervention. In a modern Security Operations Center (SOC), automation handles most of the routine tasks assigned to security analysts. This enhances the speed and efficiency of threat detection, investigation, and response while relieving human operators from the burden of manually addressing alerts. As a result, security professionals can devote more time to higher-level, strategic security tasks.
In this blog, we will discuss security automation. Additionally, we will examine how AI redefines threat detection and response.
Understanding Security Automation
Prior to the advent of automated security processes, human security analysts were tasked with manually addressing all threats, which involved meticulously investigating numerous alerts, enhancing them with threat intelligence, and deciding on appropriate actions for containment and remediation. With the vast number of alerts received today, such extensive manual intervention is impractical. Additionally, many alerts may initially seem significant but are ultimately unrelated to actual cyber threats or malicious activity. This results in analysts spending valuable time on false positives, leading to alert fatigue and diverting focus from more critical tasks.
Automation in security is using software tools and technologies to perform security-related tasks automatically. This process does not require human intervention. Security automation involves the automatic detection, investigation, and remediation of cyber threats, either with or without human intervention, using specialized programmatic solutions. It operates by identifying threats to an organization’s security posture, categorizing and prioritizing them, and then taking appropriate actions in response. This process is crucial for managing the high volume of alerts that security teams encounter daily, significantly streamlining their workload.
How It Streamlines Processes
- Faster Incident Response: Automated technologies enable you to discover security incidents in real-time. This significantly reduces the time required to contain and neutralize threats, making you safer.
- Reduced Manual Workload: You can automate mundane processes like log analysis, vulnerability scanning, and alerts. This makes it easy for you to focus on strategic activities.
- Accuracy Improved: Automation reduces the risk of human error. Thus, you can accurately detect threats.
- Consistency: Using automated tools ensures that you follow the security processes consistently. In most scenarios, this consistency plays a significant role in maintaining compliance and enforcing security policies throughout an organization so that you can be confident with the system.
In enterprises, security encompasses various layers to safeguard data, systems, and operations. A holistic approach should be followed to implement security at various layers. Security must be implemented at the network level, endpoints, application, data, and cloud.
As cyberattacks become more sophisticated and frequent, manual security measures often fall short, leading to slower response times and higher risk of breaches. Cybersecurity automation addresses these challenges by leveraging advanced technologies to streamline and optimize security processes. This approach allows organizations to automate routine tasks such as threat detection, incident response, and vulnerability management, enabling faster, more accurate responses to potential threats. By integrating automation into their security strategies, businesses can not only improve their overall security posture but also free up valuable resources for more strategic initiatives.
Now let us explore how security automation helps to address cyberthreats.
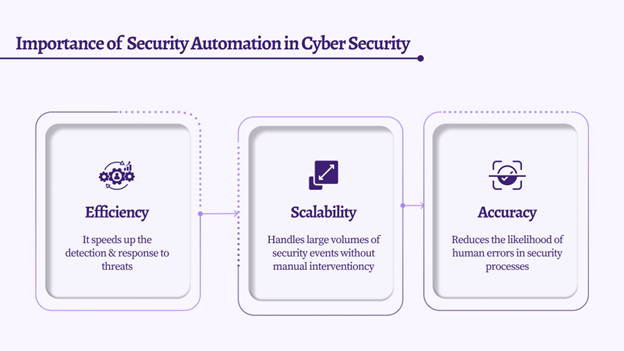
Importance of Security Automation in Cybersecurity
Security automation in cybersecurity is critical for effectively managing threats and protecting systems.
- Efficiency: It speeds up the detection and response to threats.
- Scalability: Handles large volumes of security events without manual intervention.
- Accuracy: Reduces the likelihood of human errors in security processes.
In other words, automation in network security would improve network security operations’ efficiency. This would also make them more accurate and reliable, forming the core of modern cybersecurity strategies designed for your safety.
Now that you understand security automation, let’s look at the key components that make it effective.
Key Components of Security Automation
Automation in security employs tools and scripts to do repetitive security activities without human interaction. The critical components of security automation are:
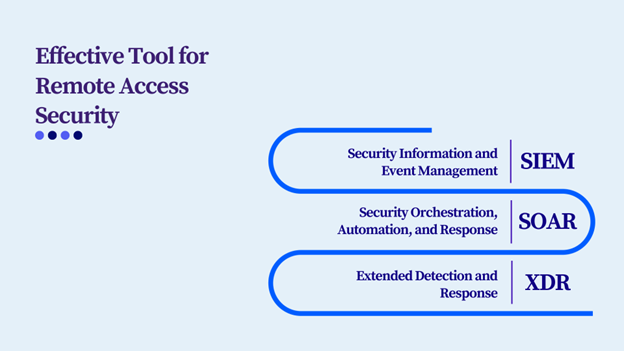
Security Information and Event Management (SIEM)
SIEM systems are essential for collecting, evaluating, and correlating data from diverse sources across an organization’s network. They enable real-time monitoring and alerting using predetermined criteria.
SIEM collects logs from devices, apps, and networks, analyzes them, and detects patterns that could signal a security concern. It then generates notifications so that security professionals can examine them further.
Consider a financial services organization using SIEM to track transactions across its network. When the system identifies an unusually high number of failed logins attempts from multiple locations, it issues a warning, requiring an immediate investigation.
Security Orchestration, Automation, and Response (SOAR)
SOAR technologies go beyond SIEM to automate the response to security issues. They connect multiple security solutions, allowing automated workflows to manage incident response without requiring human participation.
SOAR can automatically isolate compromised systems, block malicious IP addresses, and inform critical stakeholders using predefined workflows.
Let us look at an example to comprehend this notion better. When a SOAR system detects a phishing assault, it automatically quarantines the offending email, disables the user’s credentials, and alerts the IT staff to investigate the situation.
Extended Detection and Response (XDR)
XDR goes beyond typical endpoint detection and response (EDR) by integrating data from the entire security stack, including networks, servers, and cloud environments.
XDR gives a single view of the security landscape, combining data from diverse sources to help detect and respond to attacks more effectively.
Consider this: a software business utilizing XDR discovered an abnormality in network traffic patterns that pointed to a possible ransomware attack. The technology automatically isolated the vulnerable network section and launched a response mechanism to prevent the ransomware from spreading.
Difference Between SIEM, SOAR, and XDR
| Component | Primary Function | Automation Level | Ideal Use Cases |
| SIEM | Aggregates and analyzes security data | Moderate | Real-time monitoring, threat detection |
| SOAR | Automates incident response workflows | High | Incident response, threat intelligence management |
| XDR | Integrates data across the security stack | Very High | Comprehensive threat detection and response |
Implementing Security Automation: Best Practices
Implementing security automation requires careful planning and execution to ensure success. Here’s a breakdown of the best practices:
Visual Workflow:
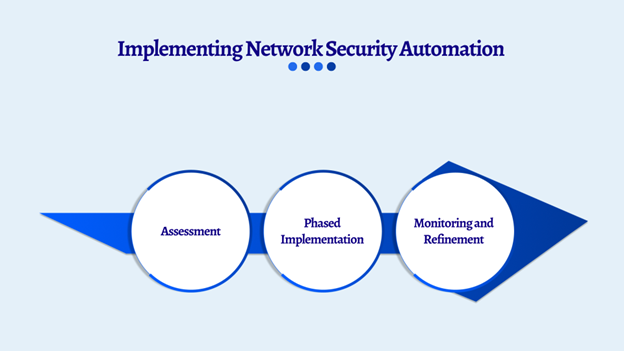
- Assessment → 2. Phased Implementation → 3. Monitoring and Refinement
Comprehensive Security Assessment: The purpose of identifying automation opportunities is to enhance security measures by assessing current tools and identifying gaps. Best practices for this process include conducting a comprehensive review of existing security tools and processes to understand their effectiveness. Focus on identifying repetitive and time-consuming tasks that could be streamlined through automation. Lastly, evaluate the potential impact of automation on the overall security posture to ensure that it improves efficiency without compromising security.
Phased Implementation: The purpose of gradually introducing automation is to reduce risks associated with its implementation. Best practices involve starting with low-risk tasks, such as log analysis or vulnerability scanning, to ensure a smooth transition. It’s crucial to test automation tools in controlled environments before full deployment to identify any issues early on. As confidence in the tools grows, gradually expand the scope to include more complex processes, ensuring that automation enhances efficiency while maintaining security and operational stability.
Continuous Monitoring and Refinement: The purpose of ensuring that automated systems remain effective against evolving threats is critical for maintaining robust security. Best practices include regularly monitoring the performance of automated tools to detect any issues or inefficiencies. Continuously update automation rules and workflows based on new insights and emerging threats to keep systems current and effective. Additionally, conduct regular audits to ensure both compliance with security standards and the overall effectiveness of the automated systems in safeguarding against threats.
Challenges and Considerations
Automation in network security brings many benefits, but it also has challenges. These challenges include:
- Integration issues
- Keeping systems updated
- Dealing with false positives
- Maintaining human oversight
Integration with Existing Systems
One of the main challenges in implementing network security automation is ensuring it integrates with existing systems. Many organizations have a mix of legacy systems and modern applications, which can make integration complex and time-consuming. Here are some of the challenges you should consider:
- Different systems may use varying protocols. It may be challenging to integrate them into a unified automated security framework.
- Existing systems may operate in silos, which can hinder the flow of information necessary for effective automation.
Initial Setup Costs and Management
The initial setup of security automation can be costly regarding financial investment and time. Organizations must purchase or develop automation tools, train staff, and possibly overhaul existing processes. These are some of the considerations you should consider:
- High-quality automation tools can be expensive; additional fees may include licenses, maintenance, and upgrades.
- Automated systems require ongoing management to function correctly and adapt to new threats.
Skill Development and Training
Automation in network security requires a skilled workforce who knows how to work with new tools and processes. It is also necessary to continually train workers because of evolving threats and automation system updates. Following is a few of those challenges:
- The IT staff might not have the necessary skills to manage automated systems. Therefore, you should provide extensive training or specialized hiring.
- As automation tools evolve, continuous education about them is also essential for the security team to use and manage them effectively.
Keeping all the challenges in mind, let us now understand how AI plays a significant role in security automation.
The Role of AI in Security Automation
Artificial Intelligence (AI) and Machine Learning (ML) improve security automation by facilitating systems’ analysis of vast portions of data and identifying patterns that would be difficult for humans to detect. These technologies are beneficial for predicting and mitigating complex threats. The key areas where AI enhances automation in security:
Predictive Analytics: Artificial intelligence can use previous data to anticipate prospective security problems and offer preemptive steps.
Anomaly detection: Machine learning algorithms can learn conventional behavior patterns and highlight deviations, allowing them to spot previously unknown hazards.
Automated Decision-Making: AI systems can autonomously decide what measures to take during an incident. These could include isolating a hacked system or preventing suspicious traffic.
Use Cases of Security Automation
Security automation automates repetitive security processes. This helps you to lower human error and enhance productivity. Now, let’s look at some common-use scenarios.
Automating Compliance Management
Compliance management is crucial for network security, especially for firms that handle sensitive healthcare, banking, and government data. Security automation may help with compliance by automating data collection, reporting, and policy enforcement.
- Security automation tools can automatically generate compliance reports. This ensures they are up-to-date and accurate.
- Automation confirms that every system follows your security policies.
Enhancing Threat Detection and Incident Response
One of the most significant advantages of security automation is enhanced threat detection and incident response. Automated systems can continuously monitor networks, detect potential threats in real-time, and respond to issues faster than manual operations.
- Automated tools continuously analyze network traffic and user activity. It will detect any irregularities that might signal a danger.
- When the system identifies any danger, it automatically launches a reaction. These may include isolating a compromised machine, blocking malicious IP addresses, or informing the security team.
Streamlining Security Operations
Automation helps security operations by taking over repetitive tasks, allowing security personnel to focus on more strategic objectives. This not only increases efficiency but also reduces the possibility of human error. Automated tools scan the network regularly for vulnerabilities, decreasing the amount of manual labor necessary and guaranteeing that all systems are up to date with the most recent security updates.
Automation can prioritize notifications according to their severity. This lets you handle the most critical concerns first, reducing alert fatigue.
Now that we’ve looked at the practical applications of security automation, we must understand the obstacles and concerns involved in implementing these solutions.
Future Trends in Security Automation
People are adopting new technologies and strategies to remain proactive against threats. Let’s explore some trends that are shaping its future.
Technological Advancements
Innovative technologies such as AI/ML are increasingly becoming crucial to security automation. These developments will enable systems to detect and respond to known threats and anticipate and address new, emerging risks.
Here are some predictions for the future:
- Enhanced capabilities will help identify potential risks before they escalate into active problems.
- Security systems will adapt to changing threat environments in real time, improving the effectiveness of automated responses.
Also read our latest blog on Cloud Security Automation
Integration of Advanced Tools
The incorporation of tools such as XDR is expected to become more common. This creates a unified platform that offers extensive security visibility and response functionalities.
- Future security solutions will likely merge into comprehensive platforms that integrate various functionalities.
- As these tools evolve, more processes will be fully automated, further reducing the need for human intervention.
Concluding Thoughts
Security automation is no longer an option. It has become an essential component for protecting your organization. As cyber threats become more sophisticated, you must rely on something other than manual processes. Automating detection, response, and compliance helps you maintain a strong security posture and safeguard your assets. Security automation enhances the defenses and streamline operations, helping to focus on higher-level tasks. Now is the time to invest in these technologies and protect organizations.
Calsoft being a technology-first partner with key expertise and specialist security consultants help customers to enhance the ‘detect & respond’ capabilities for their technologies, people, and processes, and offer AI/ML-based cybersecurity prevention solutions