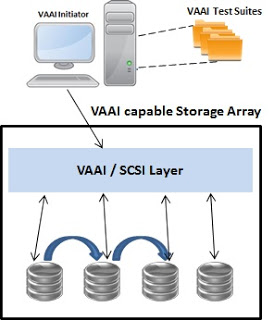
 VMware vSphere® Storage APIs – Array Integration (VAAI), also known as hardware acceleration or hardware offload APIs, are a set of APIs enabling interaction between VMware vSphere ESXi™ hosts and storage devices. The APIs in VAAI are supported by a block or NAS array (e.g. storage system) and can offload different functions from the vSphere hypervisor and virtual machine (VM).
VMware vSphere® Storage APIs – Array Integration (VAAI), also known as hardware acceleration or hardware offload APIs, are a set of APIs enabling interaction between VMware vSphere ESXi™ hosts and storage devices. The APIs in VAAI are supported by a block or NAS array (e.g. storage system) and can offload different functions from the vSphere hypervisor and virtual machine (VM).- Atomic Test and Set (ATS)
- Full Copy / XCOPY / Clone Blocks
- Data Deduplication and Full Copy
- Block Zeroing / Write Same / Zero Blocks
- Block Delete / Unmap
- Thin Provisioning Stun / TP Stun
- The below table summarizes the impact of VAAI and deduplication on a clone operation for a VM of size 10GB
|
Source LUN
|
Destination LUN
|
Remarks
|
|
|
Without VAAI
|
10 GB read
|
10 GB written
|
Utilizes both network and server
resources |
|
With VAAI (no dedupe/post-process
dedupe) |
10 GB read
|
10 GB written
|
Network and server resources
minimal. Array resources used for read and write operations |
|
With VAAI (Inline dedupe)
|
10 GB read
|
0 GB written
|
Network and server resources
minimal. Array resources spent in reads and deduplication |
|
With VAAI (QUADStor)
|
0 GB read
|
0 GB written
|
Network and server resources
minimal. Array resources spent only in deduplication |